Building OS: Linux Debian Jessie 8.0
Version: r44511 -DG15-
OpenWrt Chaos Calmer r44511
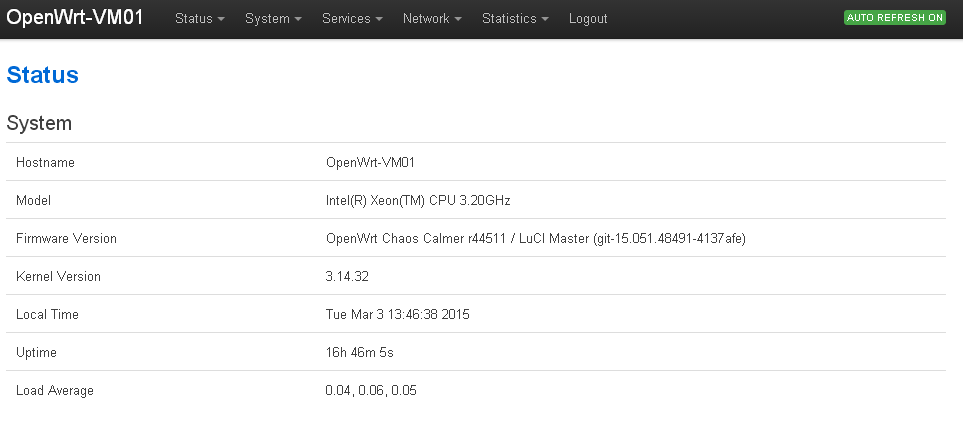
Notes:
- I used ESXi4.1 with E1000 ethernet cards for now. vmxnet3 is supported within OpenWrt, testing later.
- Make sure OpenWrt is running fine with Privoxy only (and use a DNS on WAN interface, which MUST be removed afterwards for tor-security reason!!) before install tor from OpenWrt web-interface.
Next build a CC version on another Linux Debian 8 (Jessie) machine, -DG15-
Installed the new build over the current BB version.
Tried several configurations, but most configs found on internet are for WLAN setup.
As my VM does not have a WLAN i was confused first, but after some good readings and testings found the correct setup for LAN.
My story: (read what you need is in: Current Working Configuration, below)
--
Following: https://trac.torproject.org/projects/to ... etup_notes
After several tests, port 443 can NOT be used? i used 445 instead, as any other port should work?
(https://trac.torproject.org/projects/tor/ticket/3278)
But still a name service request is NOT resolved.
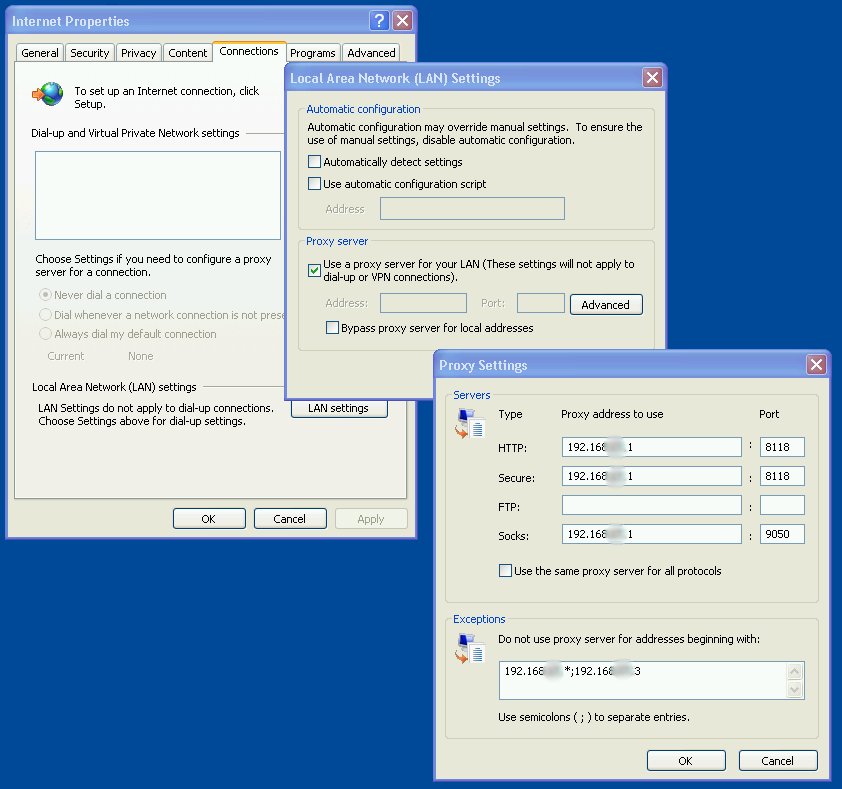
Testing now different client proxy settings (as default privoxy port 8118 is also disappeared from config ??)
Does even work worse, only another (ie, Windows) machine running Tor seems to work as proxy??
Changing proxy to OpenWrt Tor does NEVER do a name service request.
Nowhere to check these ... although enabled notification log.
Turned down Relay, as TOR does NOT do what is should.
Rebooted VM OpenWrt.
Still no success....
Found out only https is working with client Proxy settings:
Code: Select all
- http 192.168.xx.1:9050 (new)
- secure 192.168.xx.2:8118 (old)
- socks 192.168.xx.1:9050 (new)
Tested restart on commandline, this does NOT work.
Even the 'stop' command returns nothing, but TOR does not stop either!
2nd try returns
Code: Select all
# /etc/init.d/tor stop
Command failed: Not found
Changed torrc and do a reboot of the whole VM.
Next try: https://github.com/SuperBuker/tor-openwrt
Complete new setup?
After just a VM snapshot, replaced/editted all files with info from https://github.com/SuperBuker/tor-openwrt
This does the job after some adjustments!
config will follow ....
Current Working Configuration:
Make sure you have a tor network interface which looks 'floating' (ie. seems to have no connection).
In my example this is 'tor' with ip: 10.192.0.1 (Just a 'virtual' ip)
And ofcourse WAN and LAN should NOT be on same ip-range (xx.xxx.xxx.x / 192.168.xx.1) or same HW !!
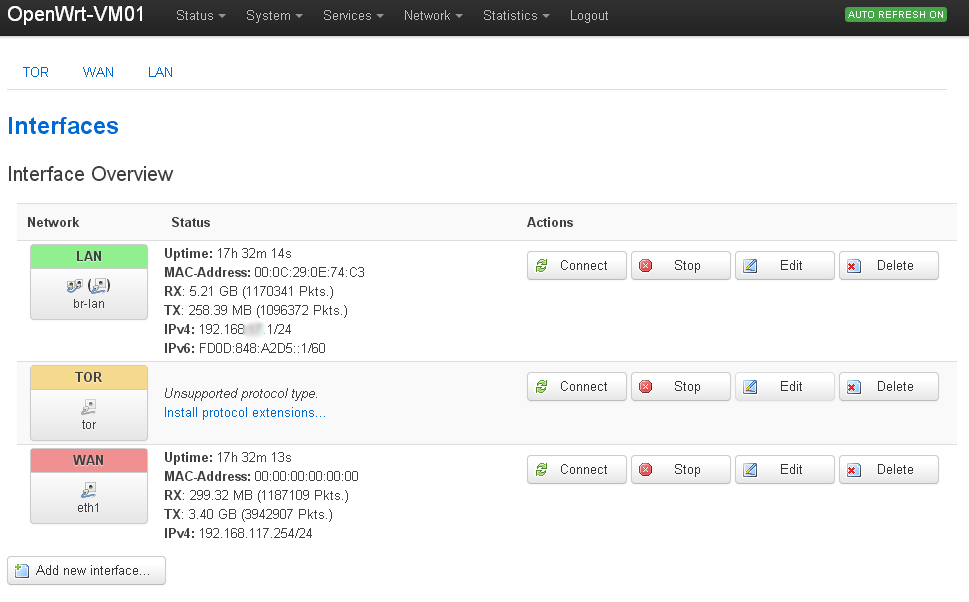
/etc/config/network
Code: Select all
config interface 'loopback'
option ifname 'lo'
option proto 'static'
option ipaddr '127.0.0.1'
option netmask '255.0.0.0'
config interface 'lan'
option type 'bridge'
option proto 'static'
option netmask '255.255.255.0'
option ip6assign '60'
option ipaddr '192.168.xx.1'
option _orig_ifname 'eth0'
option _orig_bridge 'true'
option ifname 'eth0'
config globals 'globals'
option ula_prefix 'fd0d:0848:a2d5::/48'
config interface 'WAN'
option proto 'static'
option ifname 'eth1'
option netmask '255.255.255.0'
option gateway 'xx.xxx.xxx.1'
option ipaddr 'xx.xxx.xxx.254'
config interface 'tor'
option proto 'static'
option ipaddr '10.192.0.1' # Just a 'virtual' ip
option netmask '255.255.255.0'Access Control:
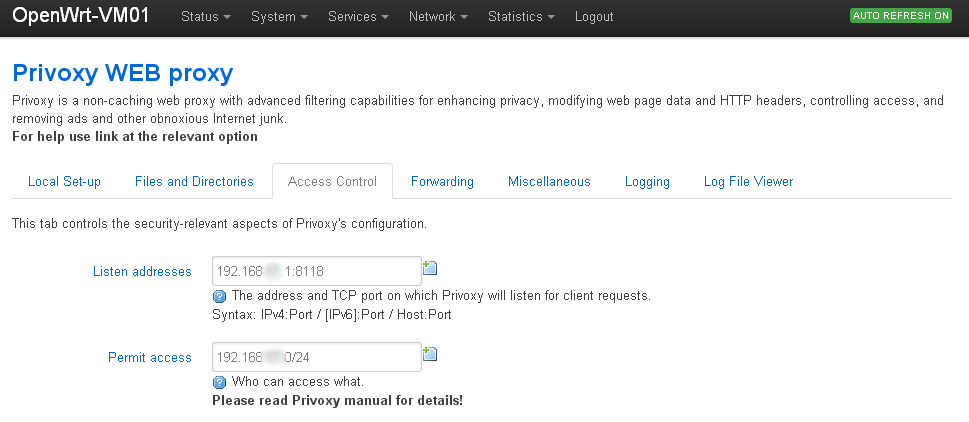
All clients within LAN are passed through Privoxy port 8118.
Forwarding (Socks 5t):
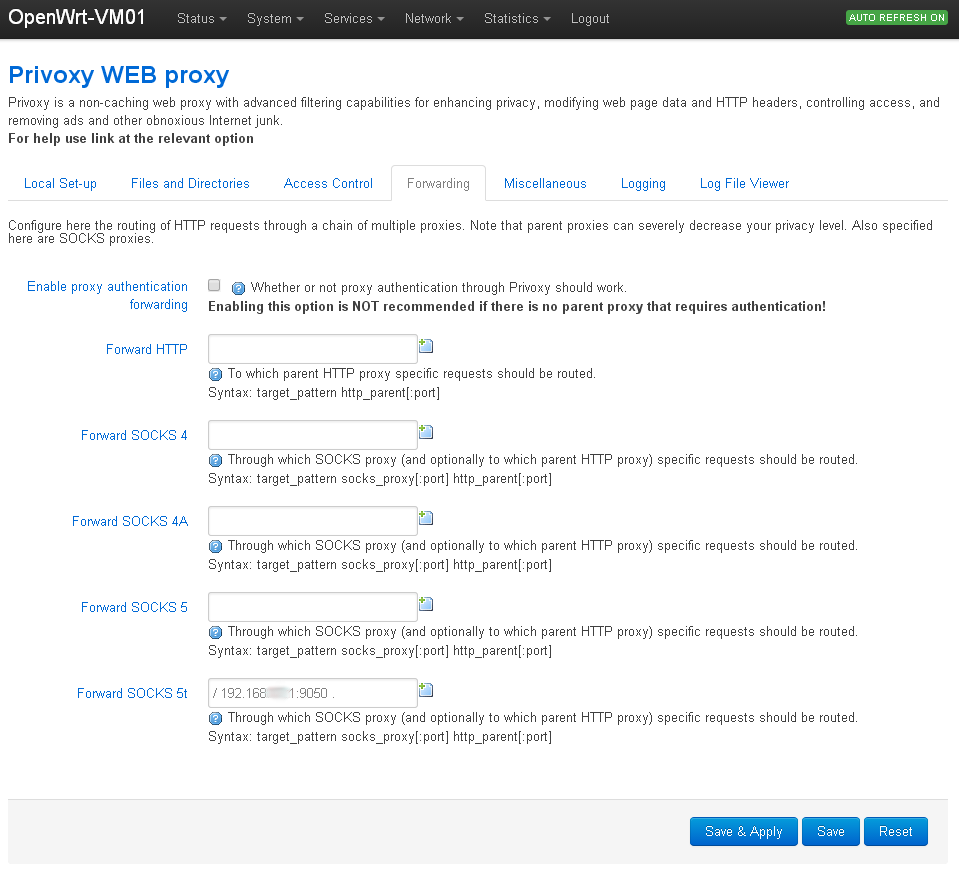
Privoxy then passes its requests to tor.
Make sure you use '/' and '.' within the string:
Code: Select all
/ xx.xx.xx.xx:[portnumber] ./etc/tor/torrc
Code: Select all
# This is a configuration for a Tor bridge on the WAN interface
# and it also runs with a transport to allow for transparent proxying
# on a specific wireless interface.
#
User tor
RunAsDaemon 1
PidFile /var/run/tor.pid
DataDirectory /var/lib/tor
# Enable entry and middle relay
# DG disabled for now ...
#
# Nickname XXXXXX
# ContactInfo XXXXXX
# ORPort 9001
# DirPort 9030
# BridgeRelay 1
# Exitpolicy reject *:* # disable exit relay
# Control port
# DG disabled for now ...
#
# ControlPort 9051
# ControlListenAddress 192.168.xx.1
# HashedControlPassword [[[Paste the hashed password]]]
# Entry Relay
# DG
#
VirtualAddrNetwork 10.192.0.0/24
AutomapHostsSuffixes .onion,.exit
AutomapHostsOnResolve 1
# SocksPort 8118 # Enable proxy socks only accesible by the private network
# As Privoxy normally uses port 8118 changed it (back) to port 9050 for 'normal' tor proxy (or any other port, only this depends on privoxy settings)
SocksPort 9050
SocksListenAddress 192.168.xx.1
TransPort 9040
TransListenAddress 192.168.xx.1
DNSPort 9053
DNSListenAddress 192.168.xx.1
# Limit middle relay shared bandwidth
RelayBandwidthRate 100 KBytes
RelayBandwidthBurst 200 KBytes
# GeoIP for stats
# DO NOT UNCOMMENT THIS LINE UNTIL GEOIP SUPPORT IS CONFIRMED
# DG disabled for now ...
#
# GeoIPFile /mnt/usb/tor/geoip/geoip
# GeoIPv6File /mnt/usb/tor/geoip/geoip6
# Logging:
# DG
Log notice file /var/log/tor/notices.log
# Log notice syslog # DG if you want tor logging into syslog, enable this rule
#
# Log notice file /mnt/usb/tor/log/notice.log
# Log debug file /var/log/tor-debug.log
# Tweaks
# Try for at most NUM seconds when building circuits. If the circuit isn't open in that time, give up on it. (Default: 1 minute.)
CircuitBuildTimeout 10
# Send a padding cell every N seconds to keep firewalls from closing our connections while Tor is not in use.
KeepalivePeriod 60
# Force Tor to consider whether to build a new circuit every NUM seconds.
NewCircuitPeriod 15
# How many entry guards should we keep at a time?
NumEntryGuards 8
# -DG- testing tor-web-services:
# Below are some http-tor-web-services tests
# Make sure the mentioned folder (/lib/tor/TMPx) is owned and used by user tor, group tor.
HiddenServiceDir /lib/tor/TMP1
HiddenServicePort 80 xx.xx.xx.xx:80
# HiddenServiceDir /lib/tor/TMP2
# HiddenServicePort 90 xx.xx.xx.xx:90
Conclusion:
Actually its the settings within: https://github.com/SuperBuker/tor-openwrt
But without:
- DHCP
- Wireless
- Firewall
- firewall.user ?
- USB
- Configure Tor
- GeoIP support
--
Other (still open) issues, when running VM OpenWrt:
Some strange network (RDP) delays which cause can not be found??
Why a delay of 1 minute now & then ??
RDP session 'hangs' but continues after about 1 minute, Putty sessions loose connection aswell as WINSCP.
--
OpenWrt DHCP server passes its own LAN address as DNS? how to prevent this?
Its no problem as OpenWrt does still no DNS request passthru.
--
OpenWrt does not run VMWare-Tools (yet) ....
--